CCIE Security Hybrid vs Physical
- Its cost effective and we have optimized and field tested all components of the lab
- You can choose between hourly and dedicated lab.
CCIE SECURITY Physical Lab
This section Covers the components of the physical lab.
Topology
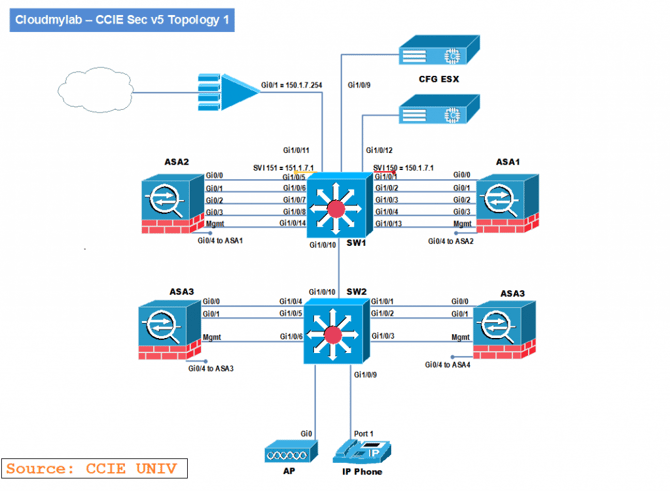
Hardware Devices used in the physical lab
Security V5 Physical Lab Equipment:
2 X Cisco Catalyst Switch C3750X- 12.2.58 SE ( Supports SXP)
2 X Cisco Adaptive Security Appliance 5512-X/5515-X: 9.6.1
1 X Cisco Aironet 3502i: 15.3.3-JC
1 X Cisco Unified IP Phone 8945: 9.2(3)
Virtual Devices hosted on ESXi Server
Cisco Identity Services Engine (ISE): 2.1.0
Cisco Web Security Appliance (WSA): 9.2.0
Cisco Wireless Controller (WLC): 8.0.133
Cisco Firepower Management Center Virtual Appliance: 6.0.1 and/or 6.1
Cisco Firepower NGIPSv: 6.0.1
Cisco Firepower Threat Defense: 6.0.1
IOSv L2: 15.2
IOSv L3: 15.5(2)T
Cisco CSR 1000V Series Cloud Services Router: 3.16.02.S
Cisco Adaptive Security Virtual Appliance (ASAv): 9.6.1
FireAMP Private Cloud
Active Directory: Microsoft Windows Server 2008
Cisco Unified Communications Manager: 8.6.(1)
CCIE SECURITY V5 Hybrid (EVE + ESXi + Physical)
CCIE Security V5 Hybrid lab has been built with a combination of technologies and has been thoroughly tested for use. We have at least 200 users at the time of writing who swear by our labs that they were able to use everything and the dedicated experience was so much cost effective and provided them with more freedom to play around
Topology- Physical Topology ( Integrated)

Hardware Devices used for CCIE-SEC V5 Hybrid Build.
1 X C3750X/3850/3650- 15.5 (Supports SXP and CTS)
1X Cisco Aironet 3502i: 15.3.3-JC
1 X Cisco Unified IP Phone79XX
1 X UCS server ( 24 CPU + 128GB RAM) with EVE-NG XL
Virtual Devices on EVE-NG XL (All VMS licensed)
All routers
All Switches
ALL ASAv
All Regular Firewalls ( Supports Clustering)
Cisco Web Security Appliance (WSA): 9.2.0
Cisco Wireless Controller (WLC): 8.0.133
Cisco Firepower NGIPSv: 6.0.1
Cisco Firepower Threat Defense: 6.0.1
Active Directory: Microsoft Windows Server 2008
Cisco Unified Communications Manager: 8.6.(1)
Active Directory: Microsoft Windows Server 2008
Dot1X and MAB PC (Simulated Behind a Physical Phone through the Physical Switch)
Cisco Web Security Appliance (WSA): 9.2.0
Virtual Devices on ESXi
Cisco Firepower Management Center Virtual Appliance: 6.0.1 and/or 6.1
Cisco Identity Services Engine (ISE): 2.1.0
FireAMP Private Cloud
Wireless Client
Additional Information
- Access lab environment - Get started with your lab
- Inside the CCIE Security Lab Topology
.png?width=70&height=55&name=Removal-642%20(1).png)
